In a world of ongoing cyberattacks, phishing attempts, and careless vendors, data security breaches at banks and credit unions are inevitable—and expensive.
The average data breach costs institutions $3.86 million, according to the IBM Security Cost of a Data Breach Report 2020, and varies based on the size of the institution.
But that’s not the only factor.
It turns out that many of the cyber risk management controls that reduce the risk of a data security breach occurring also reduce the total cost of a data breach, the report found. That means those cyber controls actually serve double duty for your bank or credit union—mitigating both data breaches and the cost of a breach.
Reducing the Cost of a Data Breach
How, then, do you reduce the cost of a breach? Make sure you have the right controls.
The two strongest controls for mitigating the cost of a data breach (regardless of industry) are incident response and business continuity management (BCM), the report found. Extensive testing of the incident response plan reduced the cost of a breach by an average of 7.6 percent. Effective BCM reduced the cost by 7.2 percent.
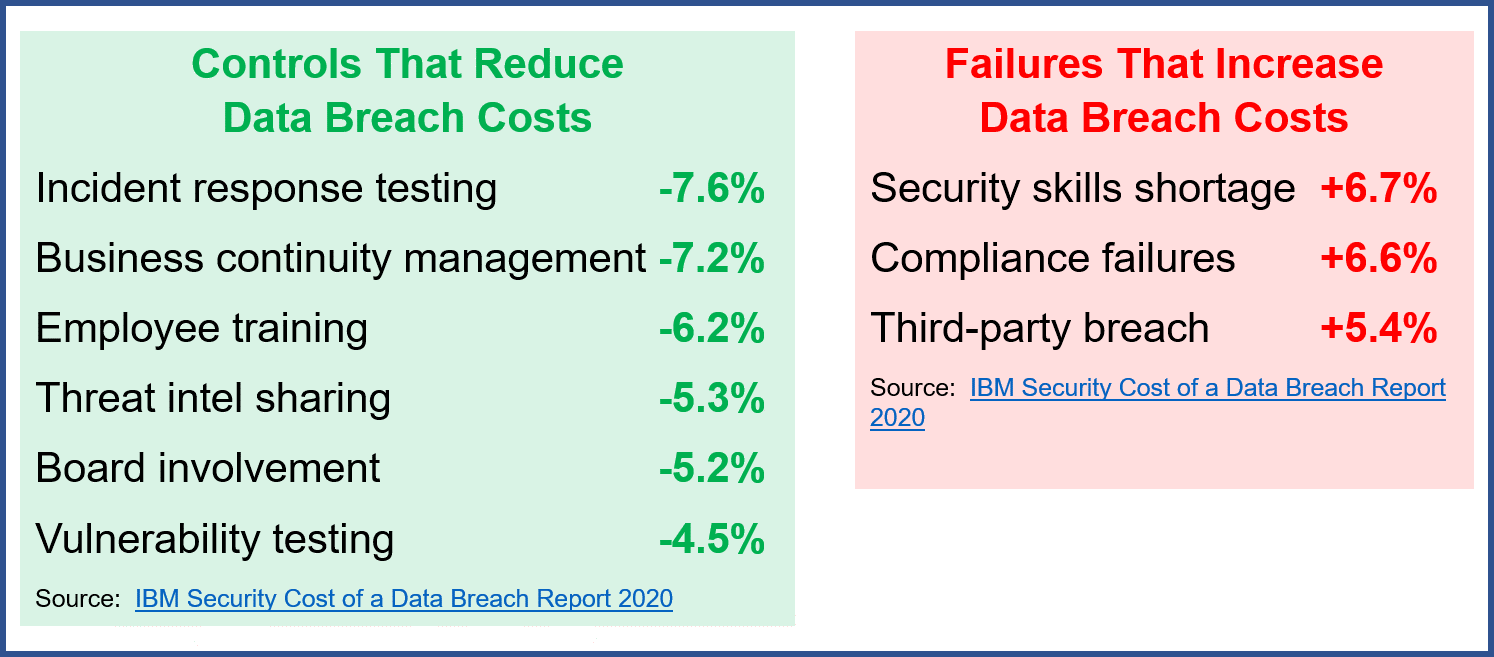
What makes these controls so effective? Banks and credit unions that have incident response plans and teams that regularly test them are more likely to swiftly identify and respond to a breach. Rather than waste time rushing together a plan, they can immediately jump into action using a plan that was carefully developed and tested with the luxury of time and forethought. This plan will have procedures for:
- Assessing and containing the incident.
- Coordinating with law enforcement and third parties.
- Restoring systems.
- Preserving data and evidence.
- Providing notification and assistance to customers.
- Facilitating the operational resilience of the institution.
It’s no wonder that the term “incident” is referenced in the FFIEC Cybersecurity Assessment Tool (CAT) 74 times.
BCM plays a similar role with business continuity mentioned three times on the first page of the Cybersecurity Maturity assessment. A business continuity plan (BCP) is all about resilience and recovery strategies. It includes function-based plans, not scenario-based plans, that address high-level problems like what happens if the institution loses a facility or a system. It gauges the impact of functions and determines how to quickly bring the functions back online.
A BCP doesn’t just say how to solve the problems. It sets specific goals, including recovery time objectives and recovery point objectives, based on a business impact analysis (BIA) to make sure there are systems to limit system downtime and data loss.
Cyberattacks are certainly capable of disrupting operations, making cyber risk considerations a key element of any BCP.
Adequate employee training and board involvement in cyber risk management can also help reduce the cost of a data breach.
Human error, including negligent employees or contractors who unintentionally cause a data breach, are responsible for 23 percent of breaches, according to the IBM study. From phishing to social engineering, employees clicking on the wrong email links, opening shady attachments, and other bad decisions are a significant source of risk. The better-trained employees are to identify and report phishing and other attempts to trick them into providing unauthorized access to systems, the better off the institution will be. Even those who open things they shouldn’t will be more likely to recognize they made a mistake and report it if they are properly trained—giving the institution a head start in addressing the breach.
Meanwhile, banks and credit unions with boards that actively oversee cybersecurity send a message to everyone at the institution that cybersecurity is a priority. These boards are more likely to understand cybersecurity, adequately fund initiatives, and follow up to make sure defenses are performing as expected. Should a breach occur, these institutions are more likely to have the other controls in place—including incident response testing, business continuity management, and employee training.
Weak Controls That Increase the Cost of a Data Breach
While effective controls can help lower the cost of a data breach at a bank or credit union, weak controls can bump up the cost. That’s especially true when it comes to compliance and third-party breaches.
Compliance failures can raise the cost of a data breach by 6.6 percent. From missing or ignored policies and procedures to ignoring regulations to forgetting to follow up on staff cybersecurity training, banks and credit unions that don’t have a strong compliance management system (CMS) can expect higher costs should a data breach occur.
Why is that? Compliance is all about adhering to rules, regulations, and internal policies—many of which are directly related to cybersecurity. A CMS is how a financial institution learns about its compliance responsibilities, incorporates them into business policies, ensures employees understand them and carry them out, and takes corrective action as needed. If a CMS results in compliance failures, it can mean that cybersecurity and BCM directives are being overlooked, making it difficult to promptly respond to a cyber event.
When a data breach is caused by a third party, it also increases the cost of the breach. Banks and credit unions need a good vendor management program that includes vendor cybersecurity due diligence. They need to identify vendors that engage in high-risk activity that requires additional oversight. They need to conduct a thorough risk assessment of a vendor’s cyber controls—a task made easier with SSAE 18 independent audit results. Banks and credit unions should also structure contracts that define terms like “potential breach,” “unauthorized access” and “breach notification” so that institutions will have the information they need to manage breaches promptly.
Without proper vendor management, banks and credit unions may not know about a breach and not be able to take action until days later—potentially putting them at risk of violating state laws with specific deadlines for notifying consumers of breaches.
What It Means for Your Bank or Credit Union
Cybersecurity isn’t just about firewalls and antivirus software. It’s about identifying cyber risks and ongoing evaluation of cybersecurity preparedness. Banks and credit unions need to know whether their existing risk management practices and controls are sufficient or whether they need further work.
The FFIEC’s CAT tool can help your bank or credit union assess its cyber maturity. Incorporating elements of the FFIEC Information Technology (IT) Examination Handbook, regulatory guidance, and the National Institute of Standards and Technology (NIST) Cybersecurity Framework, it allows institutions to evaluate cyber preparedness and know where improvements are needed.